Cloud continuous integration servers are revolutionizing software development! Forget clunky on-premise systems; cloud CI/CD lets you build, test, and deploy code faster and more collaboratively than ever before. This means less time wrestling with infrastructure and more time building awesome apps. We’ll dive into the key benefits, security considerations, and best practices for leveraging cloud CI servers to streamline your workflow and boost your team’s productivity.
From choosing the right platform to optimizing resource usage and troubleshooting common issues, we’ll cover everything you need to know to successfully implement a cloud CI/CD pipeline. We’ll also explore how cloud CI integrates seamlessly with popular DevOps tools and examine future trends shaping this dynamic field, like serverless CI/CD and AI-powered automation. Get ready to level up your development game!
Benefits of Utilizing Cloud CI Servers
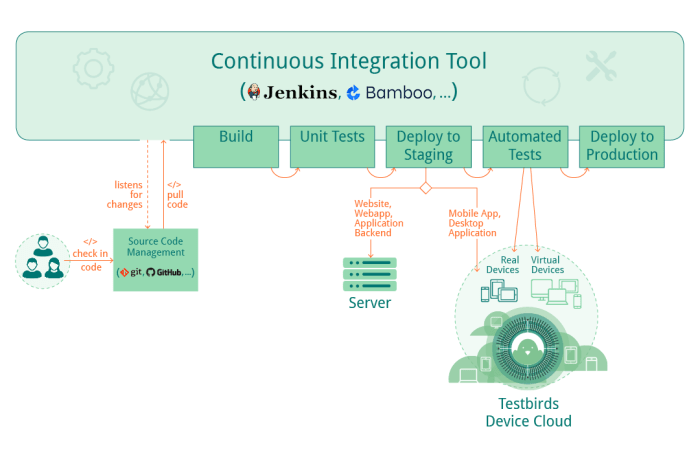
Okay, so you’re thinking about switching to a cloud-based continuous integration server. Smart move! It’s not just a trendy tech buzzword; it genuinely offers some serious advantages over traditional on-premise setups. Let’s dive into why making the switch is a game-changer for your development workflow.Cloud CI servers fundamentally change how teams work together and deploy software, offering significant boosts in efficiency and speed.
The scalability, accessibility, and built-in features are huge wins for modern development.
Enhanced Collaboration
Cloud-based CI servers foster seamless collaboration among development teams, regardless of their geographical location. Everyone has access to the same central repository and build logs, making it super easy to track progress, identify issues, and share solutions. This shared workspace eliminates the frustrating silos often found in traditional setups where developers struggle to access the necessary information or tools.
For example, a distributed team working on a large-scale project can easily contribute to the same codebase and see real-time updates, streamlining the feedback loop and accelerating development. The centralized nature also facilitates better communication and knowledge sharing, which leads to more efficient problem-solving.
Improved Efficiency and Faster Deployment Cycles
Cloud CI servers are designed for speed and efficiency. The scalability of cloud resources means you can easily scale up or down your CI/CD pipeline based on your needs, ensuring you’re never bottlenecked by resource limitations. This translates to faster build times, quicker testing, and ultimately, more frequent deployments. For instance, imagine a scenario where a traditional server struggles to handle a large build, leading to significant delays.
A cloud-based system can dynamically allocate more resources to speed up the process, minimizing downtime and accelerating the release cycle. This agility allows teams to respond more quickly to market demands and user feedback, providing a competitive edge.
Security Considerations and Best Practices
While cloud CI offers numerous benefits, security remains paramount. Adopting robust security practices is crucial. This includes utilizing strong passwords and multi-factor authentication, regularly patching and updating the CI/CD system, and employing encryption for sensitive data both in transit and at rest. Implementing access controls to limit who can access and modify the CI/CD pipeline is also critical.
Regular security audits and penetration testing should be performed to identify and address vulnerabilities proactively. Consider using tools that offer built-in security features, such as automated vulnerability scanning and compliance reporting. For example, leveraging features like secrets management to securely store API keys and other sensitive credentials within the cloud CI platform prevents accidental exposure and strengthens the overall security posture.
Real-World Examples of Successful Cloud CI Server Implementations
Many companies across diverse industries have successfully adopted cloud CI servers. Netflix, for instance, relies heavily on cloud-based CI/CD for its massive streaming platform, enabling rapid iteration and deployment of new features and updates. Similarly, companies like Spotify and Airbnb use cloud CI to manage their complex applications and ensure reliable service delivery. In the financial sector, cloud CI helps banks and fintech companies accelerate the development and deployment of secure and compliant applications.
These examples demonstrate the widespread adoption and effectiveness of cloud CI across various sectors, highlighting its versatility and value proposition.
Security and Best Practices in Cloud CI Environments
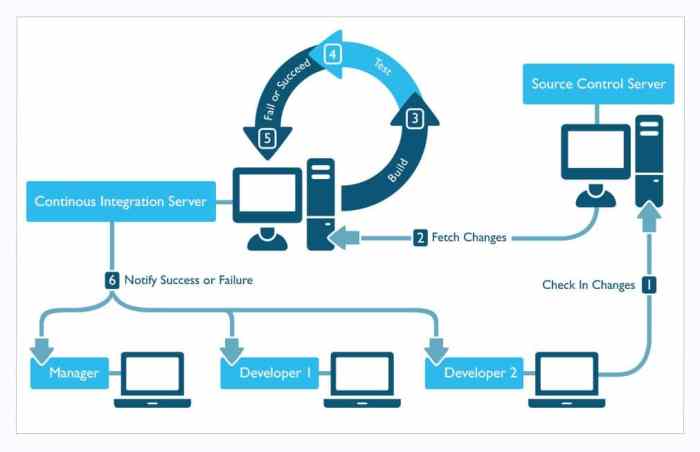
Cloud CI/CD pipelines, while offering incredible speed and efficiency, introduce new security challenges. Protecting your code, data, and infrastructure requires a proactive and multi-layered approach. Failing to do so can lead to significant breaches, data loss, and reputational damage. This section Artikels key vulnerabilities and best practices to secure your cloud CI environment.
Potential Security Vulnerabilities and Mitigation Strategies
Numerous vulnerabilities can compromise cloud CI/CD pipelines. These range from insecure configurations to malicious actors exploiting weaknesses in the system. Effective mitigation requires a comprehensive understanding of these risks and implementation of appropriate safeguards.
- Insecure Credentials: Storing passwords and API keys directly in configuration files is a major risk. Mitigation involves using secure secrets management tools like HashiCorp Vault or AWS Secrets Manager, which encrypt and manage sensitive data separately from the main codebase.
- Unpatched Dependencies: Outdated libraries and frameworks introduce known vulnerabilities. Mitigation requires regularly updating dependencies and utilizing vulnerability scanners to identify and address security flaws early in the development cycle.
- Insufficient Access Control: Overly permissive access controls allow unauthorized users or processes to access sensitive data or modify the CI/CD pipeline. Mitigation involves implementing the principle of least privilege, granting only necessary access to individuals and services.
- Compromised Build Agents: Build agents can be targets for malware or malicious code injection. Mitigation involves regularly patching operating systems, using containerized build environments, and implementing robust monitoring to detect unusual activity.
- Supply Chain Attacks: Compromised third-party libraries or tools can introduce malicious code into your pipeline. Mitigation involves careful vetting of third-party dependencies, using trusted sources, and regularly scanning for known vulnerabilities in open-source components.
Access Control and User Authentication
Robust access control and user authentication are fundamental to securing your cloud CI environment. This ensures that only authorized personnel can access and modify the pipeline and its associated resources.Implementing strong authentication mechanisms, such as multi-factor authentication (MFA), significantly reduces the risk of unauthorized access. Access control lists (ACLs) should be used to restrict access to specific parts of the pipeline based on roles and responsibilities.
Regularly reviewing and updating these controls is crucial to maintain a secure environment. For instance, a developer might only have access to their own project’s repository and build process, while an administrator would have broader access for maintenance and troubleshooting.
Implementing Security Scans and Automated Vulnerability Testing, Cloud continuous integration server
Integrating security scans and automated vulnerability testing directly into the CI pipeline is essential for proactive security. This allows for the early detection and remediation of vulnerabilities before they reach production.Tools like Snyk, SonarQube, and OWASP ZAP can be integrated to automatically scan code for vulnerabilities during the build process. These scans can identify common weaknesses such as SQL injection, cross-site scripting (XSS), and insecure authentication.
The results of these scans should trigger alerts or automatically block deployments if critical vulnerabilities are detected. This proactive approach ensures that security is an integral part of the development lifecycle, rather than an afterthought.
Securing Credentials and Sensitive Information
Protecting credentials and sensitive information within cloud CI configurations is paramount. Avoid hardcoding sensitive data directly into configuration files. Instead, leverage dedicated secrets management solutions.These solutions offer secure storage, access control, and auditing capabilities. They often employ encryption at rest and in transit, protecting sensitive information even if the underlying infrastructure is compromised. Regularly rotating credentials and implementing strong password policies further enhance security.
In this topic, you find that cloud computing uses server virtualization group of answer choices is very useful.
For example, using a secrets manager allows you to inject environment variables into your build process without ever explicitly storing the credentials in your source code. This minimizes the risk of accidental exposure or compromise.
Troubleshooting and Monitoring Cloud CI Servers
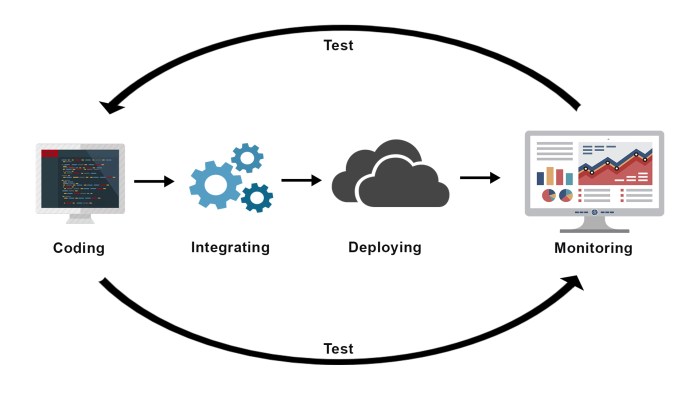
So, you’ve set up your cloud CI server, and things are mostly running smoothly. But let’s be real, hiccups happen. Knowing how to troubleshoot and monitor your system is crucial for maintaining a reliable and efficient CI/CD pipeline. This section dives into common problems, effective monitoring strategies, and practical troubleshooting techniques to keep your builds running smoothly.
Common Issues and Solutions
Troubleshooting cloud CI servers often involves identifying the source of the problem—is it a code issue, a configuration problem, a network glitch, or something else entirely? Let’s explore some typical scenarios and their fixes. One common issue is build failures due to resource constraints. If your build requires more memory or processing power than allocated, you’ll see errors.
The solution is simple: increase the allocated resources in your cloud provider’s settings. Another frequent problem is network connectivity issues. Intermittent network problems can interrupt builds or prevent the server from accessing necessary repositories. Troubleshooting involves checking network configurations, firewall rules, and DNS settings. Finally, dependency conflicts can lead to frustrating build failures.
Carefully examine your project’s dependencies and their versions to resolve inconsistencies. Using a dependency management tool like npm or Maven can help significantly.
Monitoring and Logging in Cloud CI Environments
Effective monitoring and comprehensive logging are paramount for maintaining a healthy cloud CI server. Real-time monitoring allows you to proactively identify and address issues before they impact your team’s workflow. Detailed logs provide crucial insights into the root cause of errors, helping you quickly resolve problems. Without these, debugging becomes a tedious process of guesswork. Imagine a scenario where a build fails without any logs; you’re left blindly searching for the cause.
Conversely, detailed logs pinpointing the exact line of code causing the error significantly accelerates the debugging process.
Troubleshooting Guide for Common Errors and Performance Bottlenecks
Here’s a quick guide to help navigate some common issues:
| Error Type | Possible Cause | Solution |
|---|---|---|
| Build Timeout | Insufficient resources allocated to the build process (CPU, memory, time). Complex build process. | Increase resource allocation, optimize build process (parallelization, caching), investigate and resolve bottlenecks in the build script. |
| Network Errors | Firewall issues, DNS resolution problems, connectivity problems with external services (e.g., Git repositories, artifact repositories). | Check firewall rules, verify DNS settings, check network connectivity, investigate any issues with external services. |
| Dependency Conflicts | Incompatible versions of libraries or dependencies. | Carefully review dependency versions and resolve conflicts using a dependency management tool. |
| Disk Space Exhaustion | Build artifacts, logs, or caches consuming excessive disk space. | Regularly clean up old build artifacts and logs. Configure automated cleanup scripts. Increase disk space allocation. |
Effective Monitoring Tools and Techniques
Several tools can significantly enhance your monitoring capabilities. Cloud providers often offer built-in monitoring dashboards that provide insights into resource usage, performance metrics, and error rates. These dashboards often include visualizations such as graphs and charts, allowing for quick identification of trends and anomalies. Beyond the provider’s tools, consider integrating dedicated monitoring solutions like Prometheus and Grafana for more granular control and customized dashboards.
These tools allow for the creation of alerts based on predefined thresholds, ensuring you’re notified immediately when issues arise. For example, you might set an alert to trigger if CPU usage exceeds 90% for an extended period, signaling a potential performance bottleneck. Another useful technique is logging all build events to a central logging system like Elasticsearch, Kibana, and Fluentd (the ELK stack).
This centralized logging provides a single point of access for analyzing build history and troubleshooting issues.
Ultimately, embracing cloud continuous integration servers is about more than just faster deployments; it’s about empowering your team to work smarter, not harder. By understanding the benefits, addressing security concerns, and optimizing your resources, you can unlock the true potential of cloud CI/CD and build better software, faster. So ditch the headaches of managing your own servers and let the cloud do the heavy lifting – your future self will thank you!
Question Bank: Cloud Continuous Integration Server
What’s the difference between SaaS and PaaS CI/CD solutions?
SaaS (Software as a Service) CI/CD platforms like CircleCI or GitLab CI are fully managed, requiring minimal setup. PaaS (Platform as a Service) solutions offer more customization but demand more hands-on management.
How do I choose the right cloud CI server for my project?
Consider factors like project size, budget, team expertise, and the specific tools you use. Start with a free tier or trial to test different platforms before committing.
What are some common security pitfalls to avoid?
Avoid hardcoding credentials, implement robust access control, regularly update your tools, and use automated security scanning within your pipeline.
How can I monitor my cloud CI server’s performance?
Most cloud CI platforms provide built-in dashboards for monitoring build times, resource usage, and error rates. Consider integrating with external monitoring tools for more comprehensive insights.