Cloud computing uses client server architecture true or false – Cloud computing uses client-server architecture: true or false? That’s the million-dollar question, right? Turns out, it’s way more nuanced than a simple yes or no. Think about it – you’re using apps like Netflix or Gmail all the time, and they’re totally cloud-based. But how do all those billions of requests get processed?
It’s a complex dance between your device (the client) and massive server farms (the servers) spread across the globe. We’ll dive into the nitty-gritty of how client-server architecture forms the backbone of most cloud services, exploring different models and the security implications along the way. Get ready to level up your cloud knowledge!
From the fundamental components of client-server architecture to the intricacies of cloud service models like IaaS, PaaS, and SaaS, we’ll unpack the relationship between clients and servers in the cloud. We’ll examine how different deployment models (public, private, hybrid) affect this interaction, and even explore alternatives like serverless architectures. By the end, you’ll have a solid grasp of how your favorite cloud apps work under the hood.
Client-Server Interactions in Cloud Computing
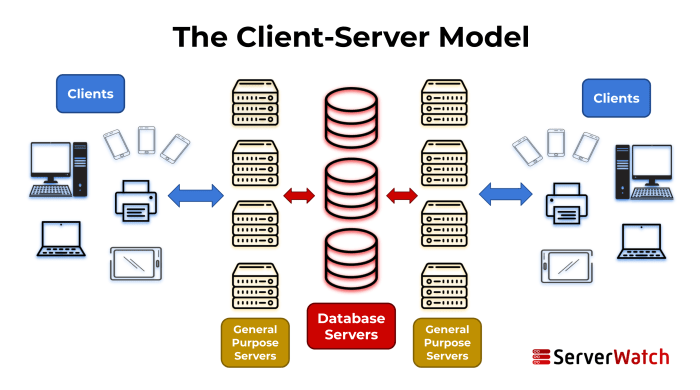
Cloud computing relies heavily on the client-server model, where clients request services and data, and servers provide them. Understanding how these interactions occur is crucial for grasping the power and potential vulnerabilities of cloud systems. This section will explore the various methods of interaction, their security implications, data transmission, and potential vulnerabilities.Client-Server Interaction MethodsClients interact with cloud servers in several ways, each with its own strengths and weaknesses.
These methods shape how data is exchanged and the level of security required.
Methods of Client-Server Interaction
Clients access cloud services through various interfaces, including web interfaces, APIs (Application Programming Interfaces), and mobile applications. Web interfaces provide a user-friendly graphical way to interact with cloud services, such as accessing files or managing virtual machines. APIs offer a programmatic way for applications to interact with cloud services, enabling automation and integration. Mobile apps provide a convenient way to access cloud services on the go, often tailored to specific tasks.
Security Implications of Different Interaction Methods
The security implications vary significantly depending on the chosen interaction method. Web interfaces, while user-friendly, can be vulnerable to cross-site scripting (XSS) attacks and other web-based vulnerabilities if not properly secured. APIs, while powerful, require careful authentication and authorization mechanisms to prevent unauthorized access. Mobile apps present a unique challenge, as they often handle sensitive data and may be vulnerable to malware or compromise if not properly developed and secured.
A well-designed security architecture needs to account for these diverse entry points and employ robust security measures for each. For example, multi-factor authentication and encryption are critical regardless of the chosen method.
Data Transmission and Processing
Data transmission between clients and cloud servers typically involves various protocols, such as HTTP/HTTPS for web interfaces and REST for APIs. Data is often encrypted during transmission to protect its confidentiality. Once received by the server, data is processed according to the specific request. This processing might involve storing the data, performing calculations, or retrieving other data. The processed data is then transmitted back to the client, again often encrypted.
Consider, for example, a user uploading a photo to a cloud storage service. The photo is encrypted during upload, stored securely on the server, and then the encrypted URL is returned to the user for access.
Potential Vulnerabilities in Client-Server Communication
Effective security practices are paramount, but vulnerabilities still exist. A thorough understanding of potential threats is vital for mitigation.
Several vulnerabilities can compromise client-server communication in cloud environments:
- Man-in-the-middle (MITM) attacks: An attacker intercepts communication between the client and server, potentially stealing data or injecting malicious code.
- SQL injection: Malicious code is injected into database queries, potentially allowing an attacker to access or modify data.
- Cross-site scripting (XSS): Malicious scripts are injected into websites, allowing an attacker to steal user session cookies or perform other malicious actions.
- Denial-of-service (DoS) attacks: An attacker floods the server with requests, making it unavailable to legitimate users.
- Data breaches: Unauthorized access to sensitive data stored on the cloud server.
- Insecure APIs: Poorly designed or implemented APIs can expose sensitive data or functionality to unauthorized access.
- Lack of proper authentication and authorization: Insufficient measures to verify user identity and control access to resources.
Alternatives to Client-Server in Cloud Computing: Cloud Computing Uses Client Server Architecture True Or False
Okay, so we’ve talked about the classic client-server model in the cloud. It’s a workhorse, sure, but it’s not the only game in town. Let’s explore some alternatives that are shaking things up in the cloud computing world. These approaches offer different trade-offs in terms of scalability, cost, and maintainability, making them suitable for various applications and needs.
Moving beyond the traditional client-server model opens up a world of possibilities for building more flexible, efficient, and scalable cloud applications. These alternatives often leverage the inherent strengths of cloud platforms to achieve greater agility and cost-effectiveness. We’ll examine two prominent examples: serverless architectures and microservices.
Serverless Architectures, Cloud computing uses client server architecture true or false
Serverless computing is a paradigm shift. Instead of managing servers, developers focus solely on writing and deploying code. The cloud provider handles all the underlying infrastructure, automatically scaling resources based on demand. This means no more worrying about server provisioning, patching, or scaling – the cloud provider takes care of it. Functions, triggered by events (like a file upload or a database change), execute independently, only consuming resources when actively processing requests.
This “pay-per-use” model significantly reduces operational costs, especially for applications with fluctuating workloads. Examples include AWS Lambda, Google Cloud Functions, and Azure Functions. These services allow developers to deploy small, independent pieces of code that are executed only when needed, resulting in a highly efficient and cost-effective solution.
Microservices
Microservices represent a different approach to application architecture. Instead of building a monolithic application, developers break down the application into small, independent services that communicate with each other over a network. Each microservice focuses on a specific business function, making them easier to develop, test, deploy, and scale independently. This approach increases agility, allowing for faster development cycles and easier updates.
Netflix, with its massive and complex streaming platform, is a prime example of a company that leverages microservices extensively. Their architecture allows them to independently update and scale different parts of their system, ensuring high availability and responsiveness.
Comparison of Architectures
Let’s compare the scalability, cost, and maintainability of client-server architecture with serverless and microservices.
| Feature | Client-Server | Serverless | Microservices |
|---|---|---|---|
| Scalability | Can be challenging; requires careful planning and resource provisioning. | Highly scalable; automatically scales based on demand. | Highly scalable; individual services can be scaled independently. |
| Cost | Can be high, especially with idle resources. | Pay-per-use model; cost-effective for fluctuating workloads. | Can be cost-effective if managed properly; requires careful monitoring and optimization. |
| Maintainability | Can be complex for large applications; requires coordinated updates. | Easier to maintain; updates are typically isolated to individual functions. | Easier to maintain than monolithic applications; allows for independent updates and deployments. |
So, is cloud computing based on client-server architecture? The short answer is a resounding YES, but with important caveats. While alternative architectures are emerging, the core principles of client-server interaction remain central to how most cloud services function. Understanding this fundamental relationship is key to grasping the complexities of cloud computing, from security considerations to scalability challenges. We’ve explored the different models, the interactions, and even the potential vulnerabilities.
Now go forth and build amazing cloud-based applications!
Detailed FAQs
What are some examples of client-server interactions in cloud computing outside of web apps?
Think mobile apps accessing cloud databases, IoT devices sending data to cloud servers for analysis, or even desktop software using cloud storage.
How does security differ between different client-server interaction methods in the cloud?
APIs generally offer more robust security features than simple web interfaces, but all methods require careful consideration of authentication, authorization, and data encryption.
What are the main drawbacks of using a traditional client-server architecture in the cloud?
Scalability can be a challenge, and single points of failure can create bottlenecks. Cost can also be a concern, especially for large-scale deployments.