Cloud configuration server could not be verified – Cloud configuration server could not be verified? Ugh, total bummer. This happens more often than you’d think, especially when you’re juggling a million things (like, you know, actually
-doing* your coursework). It’s like your server’s throwing a major fit, refusing to play nice with the cloud. We’ll break down why this happens, how to fix it, and—most importantly—how to avoid this headache in the future.
Think of this as your ultimate troubleshooting guide, straight from the trenches of college-level tech struggles.
This error can stem from a variety of issues, from simple network hiccups to more complex certificate problems or even security breaches. We’ll cover everything from basic troubleshooting steps—checking your internet connection, seriously, do that first—to digging into server logs and understanding the roles of SSL/TLS certificates. We’ll also explore how different cloud providers (AWS, Azure, GCP—you know the drill) handle this specific issue, providing you with provider-specific solutions and workarounds.
Understanding the Error Message
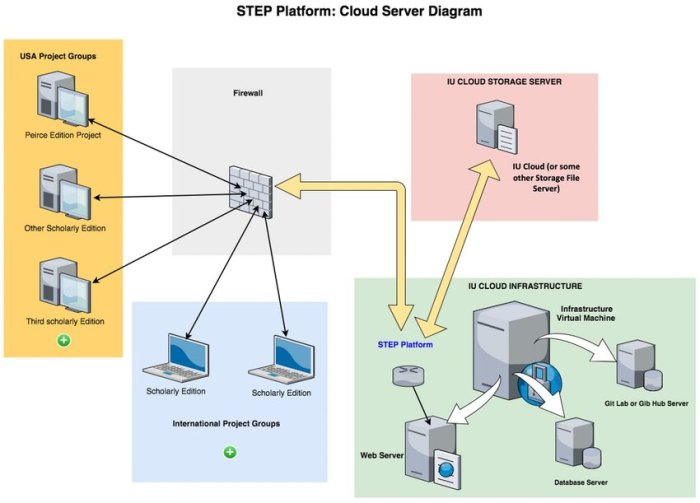
The “cloud configuration server could not be verified” error is a frustrating but common problem encountered when setting up or interacting with cloud-based systems. This error indicates a failure in the process that confirms the authenticity and proper configuration of the server you’re trying to access or utilize. Understanding the underlying causes is crucial for effective troubleshooting.The core issue stems from a mismatch or disruption in the communication and validation process between your client (your application or system trying to connect) and the cloud configuration server.
This process involves several critical components working in harmony. A failure at any point in this chain can trigger the error.
Explore the different advantages of cloud computing versus client server that can change the way you view this issue.
Components Involved in Cloud Server Verification
Several elements contribute to the verification process. These include the client application, the network connection, the cloud provider’s infrastructure (including the configuration server itself and associated security measures), and digital certificates or authentication tokens used to verify the server’s identity. Any problem with any of these parts can lead to verification failure. For example, a faulty network connection could prevent the client from reaching the server, while an expired certificate would prevent the client from trusting the server’s identity.
Similarly, incorrect configurations on the server or client side can also cause verification issues.
Examples of Situations Where This Error Might Occur, Cloud configuration server could not be verified
This error can manifest in various scenarios. Consider a scenario where a new application is being deployed to a cloud platform. If the application hasn’t been properly configured to trust the cloud provider’s certificates, it will fail to verify the configuration server. Another common scenario involves changes in network infrastructure. A change in firewall rules, for instance, might block the necessary communication channels between the client and the server, leading to verification failure.
Finally, a compromised server or a server experiencing an outage could also cause the verification process to fail. In a less technical example, imagine trying to access a website using an outdated browser; the browser’s security settings might prevent verification of the website’s SSL certificate, resulting in a similar error message.
Common Misconfigurations Leading to This Error
Several misconfigurations can trigger the “cloud configuration server could not be verified” error. Incorrectly configured firewall rules are a frequent culprit, preventing the client from establishing a connection with the server. Another common issue is an outdated or improperly installed SSL certificate on the server. This prevents the client from verifying the server’s identity securely. Similarly, incorrect DNS settings can prevent the client from locating the correct server IP address, resulting in the error.
Finally, inconsistencies between the client’s expected server configuration (such as hostname or port number) and the actual server configuration can also lead to verification failure. A simple typo in a configuration file, for example, could cause this type of issue.
Security Implications of Verification Failure
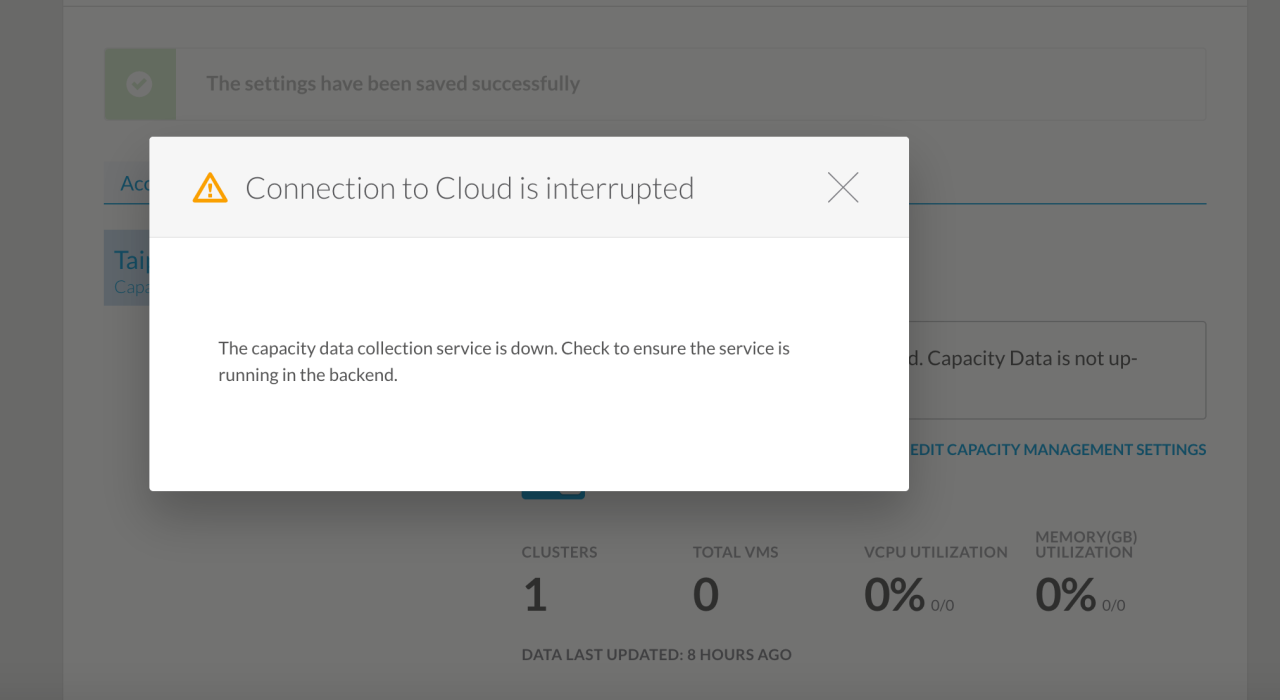
An unverified cloud configuration server presents a significant security risk, potentially exposing your organization to a wide range of attacks and data breaches. The lack of verification means that the server’s identity and configuration cannot be trusted, opening doors for malicious actors to exploit vulnerabilities and compromise sensitive information. This is far more serious than a simple inconvenience; it represents a fundamental weakness in your cloud security posture.The failure to verify the server’s configuration leaves it vulnerable to various attacks.
For example, an attacker could potentially impersonate the server, intercepting communications and manipulating data. They could also exploit misconfigurations to gain unauthorized access to the server’s resources, potentially leading to data exfiltration, system compromise, or even complete control of the server. This lack of verification could also be exploited in denial-of-service attacks, crippling your organization’s ability to access and manage its cloud resources.
A compromised configuration server can act as a pivot point for further attacks within your cloud environment.
Vulnerability Comparison
An unverified cloud configuration server’s vulnerabilities are comparable to, and in many ways more severe than, other common server vulnerabilities. Consider a SQL injection vulnerability: while damaging, it primarily affects the database. An unverified configuration server, however, affects the entire infrastructure, potentially impacting all services and data residing within the cloud environment. Similarly, a cross-site scripting (XSS) vulnerability allows attackers to inject malicious code into a web application.
However, an unverified configuration server provides far broader access, potentially allowing attackers to bypass security measures entirely and gain root access to the underlying infrastructure. The impact of an unverified configuration server is far more pervasive and potentially catastrophic.
Security Best Practices
Preventing verification failures requires a proactive approach to security. It’s crucial to establish and consistently implement robust security best practices throughout the entire server lifecycle.A strong foundation involves regularly updating and patching the server’s operating system and software, employing strong authentication mechanisms (like multi-factor authentication), and implementing strict access control measures. This minimizes the likelihood of known vulnerabilities being exploited.
Furthermore, utilizing strong encryption for all communications between the server and other systems is vital to protect data in transit. Regular security audits and penetration testing can help identify and address potential vulnerabilities before they can be exploited. Finally, implementing robust logging and monitoring capabilities allows for early detection of suspicious activity, providing the opportunity to mitigate threats before significant damage occurs.
These steps significantly reduce the risk of verification failures and subsequent security breaches.
So, you’ve wrestled with the “cloud configuration server could not be verified” error, and hopefully, you’ve emerged victorious. Remember, prevention is key. Regularly check your certificates, keep your software updated, and monitor your server logs like a hawk. Proactive maintenance is way less stressful than scrambling to fix a problem at 3 AM the night before a major deadline.
Consider this your crash course in avoiding future server meltdowns – you got this!
FAQ Resource: Cloud Configuration Server Could Not Be Verified
What if my certificate is expired?
Renew or replace your SSL/TLS certificate immediately. An expired certificate is a major security vulnerability.
Can this error be caused by a firewall?
Yes, firewalls can sometimes block necessary communication with the cloud server. Check your firewall rules to ensure they’re not interfering.
How often should I check my server logs?
Regularly! The frequency depends on your server’s criticality, but daily or at least weekly checks are a good starting point.
What if I’m still stuck after trying all the troubleshooting steps?
Contact your cloud provider’s support team. They have the tools and expertise to help you diagnose and resolve the issue.