Cloud connected servers are revolutionizing how we handle data and applications. Forget clunky on-premise systems – we’re talking seamless integration with the cloud, offering scalability, flexibility, and cost-effectiveness previously unimaginable. This exploration dives into the architecture, security, and management of these powerful tools, covering everything from choosing the right cloud deployment (public, private, or hybrid) to optimizing costs and ensuring high availability.
We’ll cover the nuts and bolts of cloud connected server setups, including network infrastructure, security protocols, and monitoring tools. Think of it as your ultimate guide to understanding and leveraging the power of cloud connectivity for your server needs. We’ll also tackle practical considerations like troubleshooting, cost optimization, and integrating your cloud server with existing systems. Get ready to level up your server game!
Security Considerations

Connecting a server to the cloud introduces a whole new layer of security challenges. Unlike a traditional on-premise server, a cloud-connected server exposes your data and applications to a much broader attack surface, encompassing both the network connecting the server to the cloud and the cloud infrastructure itself. This necessitates a robust and multi-layered security strategy.
Securing Data Transmission
Protecting data in transit between the server and the cloud is paramount. Employing strong encryption protocols, such as TLS 1.3 or its successor, is crucial. This ensures that even if an attacker intercepts the data stream, they cannot decipher its contents. Furthermore, using VPNs (Virtual Private Networks) to create encrypted tunnels between the server and the cloud provider adds an extra layer of security, protecting data from eavesdropping and manipulation even on less secure networks.
Regular security audits and penetration testing should be conducted to identify and address vulnerabilities in the data transmission process. Implementing data loss prevention (DLP) tools can help monitor and prevent sensitive data from leaving the network unauthorized.
Access Control and User Authentication
Robust access control and user authentication are essential for limiting unauthorized access to the cloud-connected server. Implementing multi-factor authentication (MFA), requiring users to provide multiple forms of verification (e.g., password and a one-time code from a mobile app), significantly reduces the risk of unauthorized logins. Principle of least privilege should be strictly enforced, granting users only the necessary permissions to perform their jobs.
Regularly review and update user access permissions to ensure they remain appropriate. Employing strong password policies and regularly auditing user accounts can further enhance security. Consider leveraging role-based access control (RBAC) to manage permissions efficiently. For example, a database administrator would have different permissions than a web developer.
Security Architecture Design
A well-designed security architecture is crucial for a cloud-connected server. This should include firewalls, both at the network perimeter and at the server level, to filter incoming and outgoing traffic, blocking malicious attempts. Intrusion detection and prevention systems (IDS/IPS) should monitor network traffic for suspicious activity, alerting administrators to potential threats and automatically blocking malicious attempts. Regular security patching and updates for both the server operating system and applications are vital to mitigate known vulnerabilities.
Consider using a web application firewall (WAF) to protect web applications from common attacks like SQL injection and cross-site scripting (XSS). Regular security audits and penetration testing should be incorporated into the security architecture to identify and address vulnerabilities proactively. Implementing a comprehensive logging and monitoring system allows for the detection and investigation of security incidents. For instance, monitoring login attempts, failed authentication attempts, and unusual network activity can provide valuable insights into potential threats.
Management and Monitoring: Cloud Connected Server
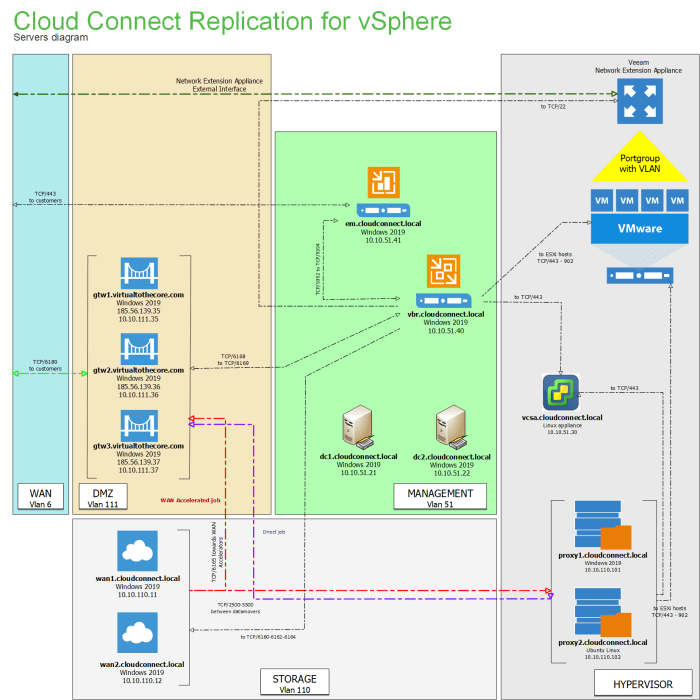
Managing and monitoring cloud-connected servers is crucial for ensuring uptime, performance, and security. Effective monitoring allows for proactive issue resolution, preventing costly downtime and maintaining a positive user experience. A multi-faceted approach, combining automated tools and manual checks, is usually necessary.
Cloud providers offer a suite of built-in tools for managing and monitoring virtual machines (VMs) and other cloud resources. These tools often provide dashboards visualizing key metrics, automated alerts, and detailed logging capabilities. Beyond the provider’s offerings, third-party monitoring solutions can enhance visibility and provide more advanced features like custom dashboards, anomaly detection, and integration with other management tools.
Techniques include using monitoring agents installed on the servers, collecting logs from various sources, and analyzing network traffic data.
Key Performance Indicators (KPIs)
Monitoring server health and performance relies on tracking specific KPIs. These metrics provide a snapshot of the server’s current state and identify potential problems before they impact users. Regular review of these KPIs allows for proactive adjustments and optimization.
When investigating detailed guidance, check out cloud config server 401 unauthorized now.
A comprehensive monitoring strategy will include a range of metrics. For example, CPU utilization, memory usage, disk I/O, network traffic, and application response times are all critical indicators. Additionally, error rates, successful request counts, and database query performance are important for application-level monitoring. Tracking these metrics helps identify bottlenecks and areas for improvement.
Implementing Automated Alerts, Cloud connected server
Automated alerts are essential for timely responses to critical events. These alerts, typically delivered via email, SMS, or other notification systems, provide immediate notification of issues requiring attention. Setting appropriate thresholds for alerts is crucial to prevent alert fatigue while ensuring timely responses to genuine problems.
Most cloud monitoring tools offer flexible alert configuration. Users can define thresholds for various KPIs and specify the notification methods. For example, an alert could be triggered if CPU utilization exceeds 90% for more than 15 minutes, or if the number of failed login attempts surpasses a predefined limit. These alerts help ensure that critical issues are addressed promptly, minimizing downtime and maintaining service levels.
Troubleshooting Common Issues
Troubleshooting cloud-connected servers often involves a systematic approach. A well-defined procedure can help to efficiently identify and resolve problems.
Effective troubleshooting requires a methodical approach, combining automated tools with manual investigation. This often begins with reviewing logs and monitoring data to identify the root cause. Then, depending on the nature of the issue, the steps may involve restarting services, adjusting resource allocation, or investigating network connectivity problems.
- Check Server Logs: Examine system, application, and security logs for error messages or unusual activity. Look for patterns or timestamps that correlate with the observed issue.
- Review Monitoring Data: Analyze metrics like CPU utilization, memory usage, and disk I/O to identify performance bottlenecks or resource exhaustion.
- Verify Network Connectivity: Ensure the server has proper network connectivity by checking IP address configuration, DNS resolution, and firewall rules.
- Restart Services: If specific services are malfunctioning, attempt restarting them. This can often resolve temporary glitches.
- Check Resource Allocation: Verify that the server has sufficient resources (CPU, memory, storage) allocated to meet its needs. Adjust resource allocation if necessary.
- Examine Security Configurations: Review firewall rules, access controls, and security group settings to ensure they are correctly configured and not blocking necessary traffic.
- Contact Cloud Provider Support: If the issue persists after attempting the above steps, contact the cloud provider’s support team for assistance.
Integration with other systems

Integrating a cloud-connected server with your existing IT infrastructure is key to maximizing its potential. This involves connecting it to various systems, both on-premise and cloud-based, enabling seamless data flow and operational efficiency. Effective integration allows for automation, improved data analysis, and a more streamlined workflow across your entire organization.Successful integration relies heavily on choosing the right APIs and protocols.
This selection depends on factors such as the specific systems involved, security requirements, and the volume of data being exchanged. Poor integration choices can lead to bottlenecks, security vulnerabilities, and ultimately, system failure.
APIs and Protocols for Integration
A variety of APIs and protocols facilitate communication between a cloud-connected server and other systems. RESTful APIs, known for their simplicity and flexibility, are commonly used for data exchange. SOAP APIs, while more complex, offer enhanced security features. Message queues, such as RabbitMQ or Kafka, are beneficial for asynchronous communication, especially when dealing with high-volume data streams.
For real-time data synchronization, WebSockets provide a persistent connection, minimizing latency. Finally, protocols like SSH and SFTP are crucial for secure file transfer. The specific choice depends on the requirements of each integration point.
Data Synchronization and Consistency Challenges
Maintaining data synchronization and consistency across multiple systems presents significant challenges. Data conflicts can arise when multiple systems update the same data simultaneously. Latency issues can lead to inconsistencies, where some systems have outdated information. Ensuring data integrity requires robust mechanisms for conflict resolution, such as version control or optimistic locking. Furthermore, careful consideration must be given to data transformation and mapping, to ensure data compatibility between different systems.
Real-time data replication strategies, while complex, can improve consistency, but increase infrastructure costs. A common example of this challenge occurs in e-commerce where order data needs to be consistently reflected across the order management system, inventory system, and payment gateway.
System Architecture: Cloud-Connected Server and On-Premise Database
A typical architecture involves a cloud-connected server acting as a middleware component. This server receives requests from various clients (web applications, mobile apps, etc.). It then translates these requests into queries for the on-premise database, using a secure connection (e.g., VPN or dedicated network link). The database responses are processed by the cloud server, and the results are sent back to the clients. This architecture allows for secure access to the on-premise database without exposing it directly to the internet. The cloud server can also perform additional functions such as data transformation, validation, and logging. Implementing robust security measures, such as encryption both in transit and at rest, is crucial for protecting sensitive data. Load balancing and failover mechanisms are essential for ensuring high availability and fault tolerance. Monitoring tools are necessary to track system performance and identify potential issues proactively.
From understanding the different deployment models to mastering security best practices and optimizing costs, this journey into cloud connected servers has equipped you with the knowledge to harness their immense potential. Remember, the key is finding the right balance between scalability, security, and cost-effectiveness. By strategically implementing the strategies discussed, you can build a robust and efficient infrastructure that adapts to your evolving needs.
So go forth and conquer the cloud!
FAQ Explained
What are the main benefits of using a cloud-connected server over an on-premise server?
Cloud-connected servers offer increased scalability, flexibility, cost savings (especially on infrastructure), and improved accessibility. They also often come with built-in redundancy and disaster recovery features.
How do I choose between public, private, and hybrid cloud deployments?
It depends on your security needs, budget, and level of control. Public clouds are cost-effective and scalable, private clouds offer more control and security, and hybrid clouds combine the benefits of both.
What are some common security threats associated with cloud-connected servers?
Common threats include data breaches, DDoS attacks, unauthorized access, and misconfigurations. Strong passwords, firewalls, intrusion detection systems, and regular security audits are crucial.
How can I monitor the performance of my cloud-connected server?
Use cloud monitoring tools provided by your cloud provider or third-party solutions. Key metrics to track include CPU usage, memory consumption, network traffic, and disk I/O.