Cloud config server 401 unauthorized – yeah, that’s a total buzzkill. This error means you’re locked out of your cloud configuration server, and it’s usually because of authentication issues. We’re talking incorrect passwords, expired tokens, or maybe even some wonky permissions. This guide breaks down everything you need to know to fix it, from checking your API keys to digging into server logs.
Get ready to become a debugging ninja!
We’ll cover common causes of the 401 error, like bad login info or expired access tokens. We’ll explore different authentication methods – API keys, OAuth, the whole shebang – and compare their security. Then, we’ll tackle troubleshooting, both on the client-side (your code) and the server-side (the actual server). We’ll even throw in some advanced debugging techniques and best practices to keep your cloud config server safe and sound.
Think of this as your ultimate guide to conquering that pesky 401 error.
Understanding the 401 Unauthorized Error: Cloud Config Server 401 Unauthorized
Okay, so you’re hitting a 401 Unauthorized error with your cloud config server. That’s a pretty common problem, and it basically means the server understands your request, but it’s refusing to grant you access because it doesn’t think you’re authorized. Let’s break down why this happens.The 401 Unauthorized error in a cloud config server context usually boils down to authentication failures.
The server needs to verify your identity before giving you access to its configuration data. If this verification process fails, you get the 401. This is a crucial security measure; otherwise, anyone could potentially access and modify your server settings.
Causes of 401 Unauthorized Errors, Cloud config server 401 unauthorized
Several factors can trigger a 401. The most frequent culprits are incorrect credentials, expired authentication tokens, and insufficient permissions. Sometimes, network issues or misconfigurations can also masquerade as a 401.
Common Scenarios Leading to 401 Errors
Let’s look at some specific situations where you’d encounter a 401. Using the wrong username or password is the most obvious one. Think of it like trying to enter a building with the wrong keycard – you’re simply not going to get in. Similarly, if your authentication token (like a JWT or OAuth token) has expired, the server will reject your request, leading to a 401.
This is a security feature designed to prevent unauthorized access after a token’s validity period has ended. Finally, even if your credentials are correct, you might still get a 401 if your user account lacks the necessary permissions to access the requested configuration data. This is like having a valid keycard, but only access to certain floors in a building – you can’t get to the restricted areas.
HTTP Request Headers Indicating a 401 Error
Analyzing HTTP request headers can often help pinpoint the root cause of a
You also can understand valuable knowledge by exploring cloud computing server technology.
401. The server’s response will include headers that can provide clues. Below is a table illustrating potential headers and their implications
| Header Name | Header Value Example | Possible Cause of 401 Error | Solution |
|---|---|---|---|
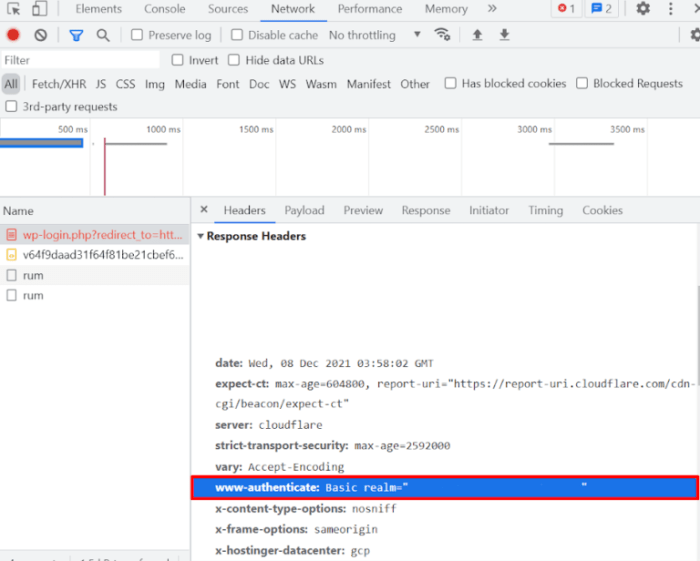
| WWW-Authenticate | Basic realm=”Config Server” | Incorrect username or password. | Verify credentials and ensure correct casing. Check for typos in the username or password. |
| WWW-Authenticate | Bearer error=”invalid_token” | Expired or invalid authentication token. | Obtain a new token using the correct authentication flow. Check token expiration time. |
| Content-Type | application/json | Insufficient permissions or incorrect API endpoint. | Check API documentation for required permissions. Verify the API endpoint is correct. |
| Status | 401 Unauthorized | Generic 401 error; further investigation needed. | Review server logs, network configuration, and authentication mechanisms. |
Troubleshooting the 401 Error
Okay, so you’re getting a 401 Unauthorized error when trying to access your cloud config server. That usually means the server isn’t recognizing your credentials. But before you start blaming the server itself, let’s check the things onyour* end – the client. Often, the problem isn’t with the server’s security, but with how your application is trying to authenticate.Client-side issues are the most common cause of 401 errors.
This means the problem lies in how your application or script is trying to connect to the server, not within the server’s configuration itself. Think of it like trying to enter a building with a faulty keycard – the building (server) is fine, but your keycard (client authentication) is the issue.
Client-Side Authentication Verification
This section details how to systematically check your client’s authentication methods to pinpoint the source of the 401 error. The process involves reviewing your API keys, access tokens, and certificates, ensuring they are correctly generated, formatted, and used within your application.
- API Keys: Double-check that you’re using the correct API key. A simple typo can cause a 401. Also, ensure the key hasn’t expired or been revoked. Many APIs have management dashboards where you can check the status of your keys.
- Access Tokens: Access tokens are often short-lived. Verify that the token hasn’t expired. If it has, you’ll need to refresh it using the appropriate API endpoint. Pay close attention to the token’s expiration time and refresh mechanisms. Incorrect handling of token expiration is a very common source of 401 errors.
- Certificates: If your application uses certificates for authentication (like TLS/SSL), make sure the certificate is valid, hasn’t expired, and is correctly configured in your application. Check the certificate’s chain of trust; a broken chain will also lead to authentication failure. Also, ensure that the certificate is correctly installed and accessible to your application.
Troubleshooting Flowchart for Client-Side 401 Errors
A structured approach is crucial for efficient troubleshooting. This flowchart Artikels the steps to systematically investigate and resolve client-side 401 errors.
- Step 1: Verify API Key/Token Validity: Check for expiration, revocation, or typos in your API key or access token. Consult your API documentation for key management tools.
- Step 2: Inspect Network Traffic: Use tools like Wireshark or browser developer tools to examine the HTTP requests sent to the server. Look for any inconsistencies in headers, especially the `Authorization` header which contains your credentials.
- Step 3: Check Certificate Validity (if applicable): Verify that your certificate is valid, unexpired, and correctly installed. Check for certificate chain issues using a certificate validation tool.
- Step 4: Review Application Code: Carefully examine the code that handles authentication. Look for potential errors in how the API key, token, or certificate is used. Pay close attention to encoding and formatting.
- Step 5: Test with a Different Client: Try accessing the server using a different client (e.g., a different programming language or a simple curl command) to rule out application-specific problems. This helps isolate whether the issue is with your application’s code or with the authentication mechanism itself.
- Step 6: Consult API Documentation: Review the API’s documentation for specific authentication requirements, including header names, formatting, and any special considerations.
Security Best Practices for Cloud Config Servers
Securing your cloud config server is paramount to maintaining the integrity and confidentiality of your entire infrastructure. A compromised config server can lead to widespread system vulnerabilities and data breaches, impacting everything from application functionality to sensitive user data. Implementing robust security measures from the outset is far more efficient than reacting to a breach.Protecting your cloud config server requires a multi-layered approach, encompassing both technical and operational safeguards.
This includes careful consideration of access control, encryption, and regular security audits. Neglecting any of these aspects significantly increases your risk profile.
Authentication and Authorization Mechanisms
Strong authentication and authorization are fundamental to securing your cloud config server. Multi-factor authentication (MFA) should be mandatory for all users, requiring at least two forms of verification (e.g., password and a time-based one-time password (TOTP) from an authenticator app). This significantly reduces the likelihood of unauthorized access, even if credentials are compromised. Authorization should be implemented using the principle of least privilege, granting users only the access necessary to perform their specific tasks.
This limits the potential damage from a compromised account. Role-based access control (RBAC) is a valuable tool for managing user permissions efficiently and effectively.
Network Security
Network security is critical for preventing unauthorized access. The cloud config server should reside in a virtual private cloud (VPC) with restricted access, limiting inbound and outbound network traffic only to necessary ports and IP addresses. Employing a web application firewall (WAF) helps to filter malicious traffic and prevent common web attacks. Regularly reviewing and updating firewall rules ensures only authorized traffic reaches the server.
Consider using a dedicated jump server to access the config server, further enhancing network security.
Data Encryption
Data encryption is crucial for protecting sensitive information stored on or transmitted by the cloud config server. All data at rest should be encrypted using strong encryption algorithms. Similarly, data in transit should be secured using HTTPS or other appropriate encryption protocols. Regular key rotation and secure key management practices are essential for maintaining the confidentiality of your data.
Security Recommendations
Implementing a comprehensive security strategy requires a proactive and ongoing approach. The following recommendations enhance the overall security posture of a cloud config server:
- Regularly update the server’s operating system and all installed software to patch known vulnerabilities.
- Implement intrusion detection and prevention systems (IDS/IPS) to monitor for suspicious activity and automatically respond to threats.
- Conduct regular security audits and penetration testing to identify and address potential weaknesses.
- Enable logging and monitoring to track access attempts and other server activity. Regularly review logs for suspicious behavior.
- Establish a robust incident response plan to effectively manage and mitigate security incidents.
- Use strong passwords and enforce password complexity requirements. Implement password rotation policies.
- Employ a version control system to track changes to configuration files and allow for easy rollback in case of errors.
- Segment your network to isolate the config server from other sensitive systems.
So, you’ve wrestled with the 401 unauthorized error and emerged victorious! By understanding the various authentication methods, performing thorough client and server-side troubleshooting, and implementing robust security practices, you’ve significantly improved your cloud config server’s security and reliability. Remember, preventing these issues is key, so stay on top of your security best practices and keep those credentials fresh. Now go forth and conquer your cloud!
Frequently Asked Questions
What if I’ve forgotten my API key?
Most cloud providers have a system for resetting or regenerating API keys. Check your provider’s documentation for instructions.
How do I know if my token has expired?
Look for specific error messages in the response from the server. Many APIs will include an expiration timestamp in their responses, or provide clear messaging indicating an expired token.
Why is my server returning a 401 even with correct credentials?
Check server-side logs for more details. There might be a misconfiguration on the server preventing authorization even with valid credentials. This could also be related to IP address restrictions.
Can I use a VPN to access my cloud config server?
Potentially, but make sure your VPN doesn’t interfere with the authentication process. Some VPNs can cause issues with authentication due to IP address changes.